Vulnerabilities and attackers are emerging faster than most organizations can keep up with in today’s hyperconnected environment. Between 2019 and 2024, the number of newly identified vulnerabilities more than doubled - from 17,000 to over 38,000 - underscoring the urgency for more efficient vulnerability management strategies.
To stay ahead, organizations must prioritize vulnerabilities based on their potential impact. “Critical” vulnerabilities are those that pose the highest risk - typically defined by their exploitability, public exposure, association with active threat campaigns, or their potential to disrupt essential business operations. These are the weaknesses attackers target first because they offer the fastest and most damaging paths to compromise.
In this landscape, simply identifying vulnerabilities isn’t enough. Maintaining a strong security posture demands continuous, prioritized, and automated remediation to close high-risk exposures before they can be exploited.
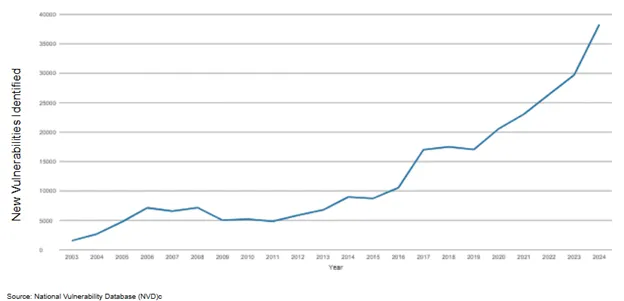
Figure 1: Year-over-Year Increase in Newly Identified Vulnerabilities
Whatever your company's size, the risk is real and increasing.
Additionally, the average period between a vulnerability's disclosure and actual exploitation has decreased to less than seven days, indicating that attackers are not waiting around. This short window increases the risk that attackers will gain unauthorized access to systems before remediation can occur, which dramatically shortens our window for decisive vulnerability remediation. To mitigate this risk, organizations must more effectively manage vulnerabilities by prioritizing and remediating them efficiently, with risk identification as the primary method for prioritization and automation as a key component in remediation.
Why Vulnerability Remediation Can’t Wait in 2025?
Cybercrime is expected to cost the world $15 trillion1 by 2030. The growing cost of cybercrime highlights the need to reduce security risks through a structured vulnerability management process. The urgency to address vulnerabilities has never been higher, especially as vulnerability exploitation surged by 34% year-over-year, now accounting for 20% of all confirmed breaches as reported by Verizon Data Breach Investigation Report 20252.
What Is Vulnerability Exploitation?
Vulnerability exploitation occurs when attackers exploit flaws in your software, systems, or configurations, also known as security vulnerabilities, to gain unauthorized access, steal sensitive data, or disrupt operations. Some of the key risks include: data loss or destruction, productivity loss, theft of personal or financial data, financial theft, intellectual property theft, and reputational damage.
Why Does It Matter?
When exploited, vulnerabilities can lead to:
- Data breaches
- System outages
- Ransomware attacks
- Financial and reputational damage
A Preventable Risk
The good news? Vulnerability exploitation is one of the few attack methods that can be completely shut down, with the right tools and processes.
That’s why having a strong vulnerability remediation strategy is critical. By identifying, prioritizing, and fixing the most dangerous weaknesses first, you can significantly reduce your exposure to attacks.
What Is Automated Vulnerability Remediation?
Picture this: You find a weak spot in your armor, right? Well, this isn't just about pointing it out. It's about seamlessly transitioning from identifying vulnerabilities to actually fixing them, all thanks to some brilliant automation.
We're talking about way more than just hitting a "patch" button; it's a strategic game-changer.
It utilizes advanced technology to quickly identify, prioritize, and deploy critical fixes across all your IT systems. The big win? It reduces those risky windows where you're left exposed and drastically reduces the amount of manual labor your team must perform. Simply put, consider it your own industrious and incredibly intelligent security team, always striving to ensure that your systems are not only visible but also genuinely and consistently secure, regardless of how large your business grows.
Why Does Vulnerability Remediation Matter More in 2025?
- The number of new vulnerabilities has increased significantly.
- IT Operations Security teams are overwhelmed with patch requests.
- Exploits can often occur within hours of public disclosure.
- Manual remediation is too slow to effectively reduce risk.
Example: July 2025: SharePoint Zero day Breach Shows Why Speed Matters In Detection And Remediation
In July 2025, a critical zero-day vulnerability, CVE-2025-53770, was discovered in Microsoft SharePoint. Within days, attackers had exploited the flaw, targeting at least 300 unpatched on-prem SharePoint servers across enterprises and government agencies.
The problem?
It took many organizations too long to detect the vulnerability in their environments, and even longer to remediate it. The vulnerability's severity was assessed using industry-standard risk ratings, such as CVSS, which influenced the urgency of the response. That delay allowed attackers to exploit the flaw before defenses were in place.
The Lesson
Organizations need to:
- Quickly identify where they are exposed to the most urgent vulnerabilities
- Swiftly remediate those exposures before attackers can exploit them
Detection alone isn’t enough. Timely action is critical. A structured vulnerability remediation process ensures vulnerabilities are addressed quickly, efficiently, and consistently.
The Problem: Visibility Without Vulnerability Remediation Equals Risk
Even if vulnerability detection and prioritization have advanced significantly, cyber intrusions still happen at a startling rate. By definition, remediation will occur after identification. The goal is to minimize that window as much as possible, utilizing a robust remediation platform that provides broad coverage to remediate vulnerabilities across various system types (i.e., a single tool rather than requiring multiple tools to patch different devices/OSes/applications), and automation that further accelerates remediation processes.
It highlights a gap in our current vulnerability management practices and the effectiveness of existing vulnerability remediation tools.
Across enterprise endpoints and servers, delayed remediation continues to be a major concern. The 2025 Verizon Data Breach Investigations Report (DBIR) underscores this ongoing gap — with vulnerabilities often remaining unpatched well beyond standard SLA timelines. The situation isn’t new; the 2024 DBIR reported that 60% of breached firms already had fixes available but never implemented them, revealing a persistent failure to translate detection into timely action. This highlights that the real challenge lies not in identifying risks, but in executing remediation swiftly and consistently.
Furthermore, a January 2025 Swimlane report3 demonstrates the continued difficulty of effective remediation: For a surprising 68% of businesses, fixing serious vulnerabilities takes more than 24 hours. This implies that self-perceived efficacy in vulnerability mitigation remains poor. As organizations face growing cyber exposure, it becomes increasingly important to understand and reduce the organization's attack surface to minimize potential entry points for attackers.
This continuous struggle highlights why simply having a vulnerability management tool isn't enough; true vulnerability remediation requires more. Modern solutions now analyze attack paths to predict and prioritize potential breach points, helping organizations proactively address the most critical risks. Organizations must actively manage vulnerabilities as part of an ongoing process to maintain security and reduce risk.
…and we know that we are not good at vulnerability remediation.
So, why is remediation still such a significant hurdle?
Well, let's break it down:
IT Teams are Overworked:
Your IT teams are stretched thinner than ever before, and frankly, they're overwhelmed! Think about it: they're constantly juggling a dizzying array of operating systems, countless applications, and literally thousands of endpoints.
And to make matters worse, they often have a different tool for each of those things!
This explosion of tools, known as “tool sprawl,” means they're not just managing systems; they're also learning, maintaining, and integrating multiple complex toolsets — each with its own nuances and limitations. This adds immense complexity, preventing consistent, streamlined processes and slowing down progress across the board.
For instance, each tool may offer varying levels of automation or coverage, forcing teams to manually coordinate activities between them. Visibility, reporting, and progress tracking then have to happen across disparate systems, increasing coordination time, introducing data delays, and making it difficult to maintain timely, accurate remediation workflows.
The numbers don’t lie: A January 2025 Swimlane report revealed that 57% of security teams spend a quarter to half of their time on manual processes such as correlating scanner data, validating exposures, and communicating remediation priorities to IT teams. These repetitive coordination efforts slow down the overall response cycle — leaving less time for actual risk reduction. Traditional patch management workflows lack automation and orchestration between Security and IT, which is why vulnerabilities continue to linger far longer than they should. This lack of integration directly fuels the communication gaps between Security and IT teams, making fast, coordinated remediation even harder to achieve.
Broken Communication Between Teams:
Security and IT teams are still often misaligned. They are using distinct playbooks or speaking different languages. In addition to slowing down quick remediation, fragmented tools and competing goals cause teams to make incorrect fixes, leaving the most serious risks unchecked. The absence of precise context and information is a major obstacle in this case.
According to the Swimlane report, 35% of organizations claim that this is actively hindering their remediation efforts, and 37% of organizations identify it as their greatest challenge when prioritizing vulnerabilities. Such disconnects cripple comprehensive security and vulnerability management.
It's a clear sign we need to build more bridges, not walls, between these crucial teams.
Disconnected Tools With Unclear Signals:
And finally, we're back to tool sprawl being rampant. Many organizations are relying on multiple, often completely disconnected, tools to manage their patching and vulnerability remediation.
This fragmentation creates a chaotic environment where getting a comprehensive overview and taking streamlined action is practically impossible. It undermines the very purpose of effective vulnerability remediation.

When you put all these factors together, what do you get?
A longer Mean Time To Remediation (MTTR), significantly higher operational risk, and steadily growing cyber exposure for organizations worldwide.
The data screams it: Just seeing the vulnerabilities isn't enough anymore. We need robust, timely, and truly integrated remediation strategies. That's the only way we'll ever close this ever-widening security gap.
What Today’s Remediation Demands?
Knowing what is exposed is not enough to address modern vulnerability risk; you also need to remediate quickly. Security and IT teams must be able to collaborate on what truly matters, prioritize tasks based on exploitability and business risk, and quickly implement reliable patches with the aid of a robust remediation approach.
We require cloud-native, intelligence-led solutions that operate in complex hybrid environments to bridge the gap between detection and action. The ideal platform should eliminate scripting bottlenecks, streamline processes across all devices, and provide transparent evidence of risk reduction to all stakeholders, from security analysts to CISOs. Prioritization, automation, and cross-team collaboration play a crucial role in effective vulnerability remediation.
Bridging The Gap: What The Right-Based Vulnerability Management Solution Looks Like
To complete the vulnerability lifecycle (discover → prioritization → remediation → validate remediation) , organizations need:
- End-to-end integration between vulnerability scanners and remediation engines
- Real-world threat data to identify risk
- Extensive automation that removes scripting and manual coordination, and accelerates remediation
- Comprehensive coverage to streamline visibility and remediation across all devices
- Clear impact tracking, including MTTR, patch success rates, and SLA adherence
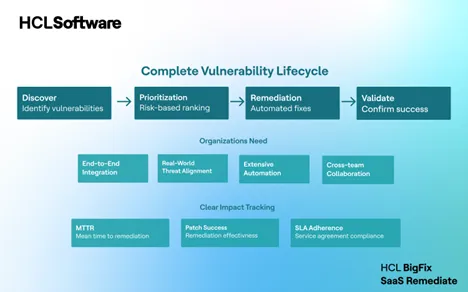
The Solution: HCL BigFix SaaS Remediate
That’s where HCL BigFix SaaS Remediate steps in.
It’s a cloud-native solution that turns vulnerability management insights into rapid remediation, purpose-built to help Security and IT Ops teams prioritize, fix, and prove their impact at scale.
Instead of tool sprawl, it brings:
- CyberFOCUS intelligence- Built-in threat context that aligns remediation with real-world risks, including CISA Known Exploited Vulnerabilities4 and MITRE Advanced Persistent Threat (APT)5 mappings.
- Protection Level Agreements (PLAs)- A first-of-its-kind capability to track remediation outcomes, including MTTR, SLA adherence, and risk reduction across environments.
- 500,000+ pre-built Fixlets- The industry’s most extensive and continuously updated remediation library, covering 100+ OS versions and CPU architectures, and 450+ third-party applications.
- Prescriptive Guidance- Automated, prioritized remediation recommendations that help teams act with confidence, not just for compliance, but for true risk closure.
You can onboard in minutes and act immediately, with no infrastructure required.
This is more than just patching. This is vulnerability and risk management with measurable security outcomes.
What Makes BigFix SaaS Remediate Different
It addresses vulnerabilities at scale, with accuracy, automation, and full-stack coverage across all endpoints. This BigFix SaaS Remediate is designed to provide visibility and take decisive action from a single, unified platform. While many vendors now offer remediation capabilities — often as loosely linked add-ons or separate modules — BigFix SaaS Remediate stands apart for its depth, breadth, and simplicity.
It delivers the broadest out-of-the-box remediation coverage across the widest range of operating systems & third-party applications, ensuring consistent, scalable remediation across complex enterprise environments. And as a true SaaS solution, it offers a seamless try-and-buy experience — enabling organizations to move effortlessly from trial to production without infrastructure setup, downtime, or workflow disruption.
This combination of scale, automation, and instant accessibility allows BigFix to address vulnerabilities faster and more accurately across all endpoints. Reactive patching is no longer enough — modern vulnerability remediation demands intelligence-driven action, measurable outcomes, and frictionless collaboration between Security, IT, and vulnerability management teams. That’s exactly where BigFix SaaS Remediate leads.
The result? Every stakeholder - from CISOs to IT admins - experiences faster time to value, measurable security outcomes, and a clear path from visibility to verified risk reduction making it a leading vulnerability remediation tool & does more than merely identify vulnerabilities.
Reactive patching is no longer sufficient for modern vulnerability remediation; instead, intelligence-driven action, quantifiable results, and seamless communication between IT, security, and vulnerability management are required.
What’s In It for You? How BigFix SaaS Remediate Serves Every Role
Whether you're a CISO defining your organization’s security strategy or an IT admin juggling daily patch cycles, HCL BigFix SaaS Remediate delivers measurable outcomes for every role across the remediation chain.
For CISOs and Cyber Risk Leaders
- Lead with resilience. Prove it with metrics.
BigFix helps CISOs confidently report on vulnerability closure and reduce boardroom anxiety over cyber risk. With Protection Level Agreements (PLAs) and CyberFOCUS dashboards, you can transform threat data into executive-level outcomes, such as reduced Mean Time to Remediation (MTTR), SLA compliance, and a proven reduction to your attack surface.
For Security Operations Teams
- BigFix SaaS Remediate enables SecOps to continuously and more quickly understand their vulnerability attack surface against potential threats, driving collaborative remediation.
For IT Operations & Endpoint Managers
- Simplify patching. Unify platforms.
Manage 100+ OS versions, remote endpoints, and complex production environments with ease. BigFix enables multi-platform endpoint patch management, with built-in automation, tested workflows, and custom remediation through scripts and policies.
For IT Procurement & Economic Stakeholders
- Fewer tools. Lower costs. Greater impact.
Reduce tool sprawl, infrastructure overhead, and security risk in one move. BigFix SaaS Remediate offers transparent pricing, scalable licensing, and a rapid ROI.
Real-World Use Case Story
See what a manufacturing customer with >100K endpoints who installed BigFix has to say:
”Security told us their scan showed zero missed vulnerabilities, but when we installed BigFix CyberFOCUS, it immediately identified over 8000 additional vulnerabilities! The Security Team was really impressed with BigFix."
Outcomes You Can Measure
|
Metric |
Result with HCL BigFix SaaS Remediate |
|
First-pass patch success rate |
>98% |
|
Faster Outcomes |
|
Final Word: Don’t Just Detect Vulnerabilities, Remediate Them at Scale.
In a world where vulnerabilities are growing 10 times faster than teams can patch, your enterprise needs more than visibility - it needs velocity, precision, and results. That’s exactly what BigFix SaaS Remediate delivers.
Remediate at scale. Collaborate across teams, simplify automated patch management, strengthen endpoint patch management, and prove your risk reduction.
Frequently Asked Questions (FAQs)
Q1. What distinguishes vulnerability remediation from patch management?
A: While deploying security patches is one common way to close vulnerabilities, patch management and vulnerability remediation are not identical.
- Patch management focuses on deploying updates to software and systems — not only for security fixes, but also to address functional issues, performance improvements, and bug resolutions.
- Vulnerability remediation, on the other hand, is broader — it involves closing security gaps, which may include deploying patches, updating configurations, disabling vulnerable services, or implementing compensating controls.
There’s clear overlap between the two, but also distinct boundaries: patch management is a subset activity that supports the broader goal of vulnerability remediation.
Q2. How quickly can BigFix SaaS Remediate be deployed?
A: No infrastructure is needed, and you can be remediating vulnerabilities within minutes of sign-up!
Q3. How does BigFix rank the vulnerabilities that need to be patched?
A: CyberFOCUS within BigFix helps organizations identify and remediate the most urgent vulnerabilities, for instance, those that real-world attackers are actively leveraging.
Q4. Is it compatible with on-premises, cloud, remote, and hybrid systems?
A: Yes! It is designed to scale from small organizations to complex hybrid enterprise environments.
Q5. Do compliance teams and CISOs have reporting?
A: Absolutely. BigFix SaaS Remediate provides comprehensive, executive-ready dashboards designed for CISOs, compliance teams, and audit stakeholders. These dashboards consolidate real-time visibility into vulnerability posture, remediation progress, and overall risk reduction.
Through Protection Level Agreements (PLAs) — a unique capability exclusive to BigFix — organizations can track and validate outcomes such as Mean Time to Remediation (MTTR), SLA adherence, patch success rates, and compliance alignment across hybrid environments.
This means compliance teams gain clear, auditable proof of remediation activity, while CISOs can communicate measurable progress to leadership and the board — turning technical remediation data into quantifiable, business-level security outcomes.
Sources:
- https://cyberdefensewire.com/cyber-attacks-surge-global-giants-face-15-trillion-threat-by-2030/
- https://www.verizon.com/about/news/2025-data-breach-investigations-report
- https://swimlane.com/blog/key-insights-is-vulnerability-management-at-its-breaking-point/
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- https://attack.mitre.org/groups/
Start a Conversation with Us
We’re here to help you find the right solutions and support you in achieving your business goals.








