In this case study, we explore how a new certificate request placed in a ticketing tool like Service Now could be managed through HWA end to end and how HWA could generate this certificate request while also placing a CSR request. Besides also raising a change in Service Now to schedule the certificate addition to the KeyStore, which was stated in the original ticket. This is done by creating and scheduling a Jobstream to automate the certificate application step on the given scheduled date and time.
Let’s examine how an application team that wants to renew its certificate on an existing KeyStore places a request in Service Now to generate a new certificate. By providing details like the date and time when the certificate is to be renewed on the application, the exact KeyStore location, KeyStore name, and certificate name.
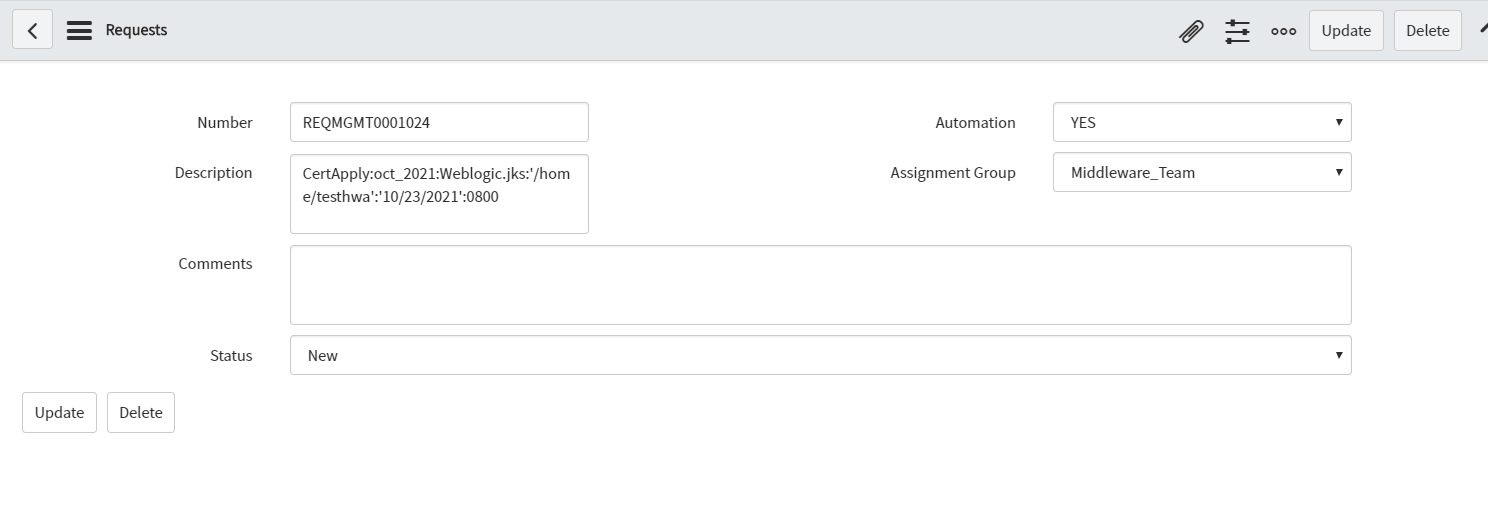 Fig1:
Fig1:
Solution Realization:
A Jobstream on HWA would process this request and generate a new certificate on the fly while also scheduling a change request on Service Now to manage this change; it would also gather details like the certificate application date, time, the KeyStore Path, KeyStore etc., to be applied on the given KeyStore while including these details in the description of the change ticket and append a generic implementation plan and backout plan in the change, it would also a create a Jobstream to apply the certificate to the application on the given date and time.
SERVICENOW_GET_CERT_DESCRIPTION:
This job would be a RESTFUL GET job which would gather a description from the SNOW Ticket filtering by Assignment Group Middleware_Team to extract details from the ticket description and redirect output to an output file /tmp/cert_request_description.
 Fig2:
Fig2:
EXTRACT_CERTPATH:
This job would extract the certificate path from the request description:
 Fig3:
Fig3:
EXTRACT_CERT_APPLY_DATE:
This job would extract the date when the certificate is to be applied on the System from the request description:
 Fig4:
Fig4:
EXTRACT_CERT_APPLY_TIME:
This job would extract the time when the certificate is to be applied on the system from the request description:
 Fig5:
Fig5:
EXTRACT_CERT_NAME:
This job would extract the name of the certificate to be applied on the system from the request description:
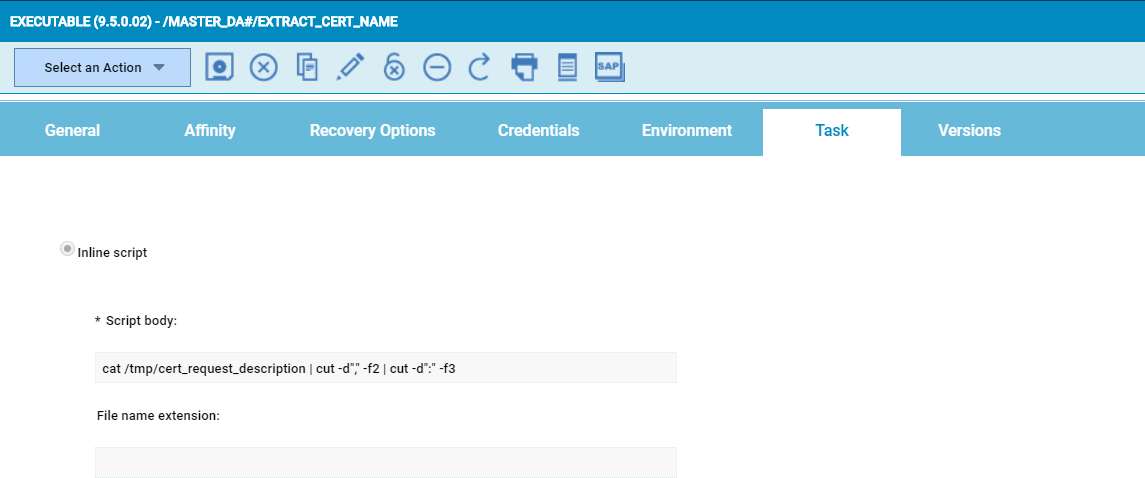 Fig6:
Fig6:
STORE_CERTPATH , STORE_CERT_APPLY_DATE , STORE_CERT_APPLY_TIME and STORE_CERT_NAME Jobs:
These STORE would use jobprop utility of HWA and store all details like certificate path, certificate application date, certificate application time and certificate name into HWA variables and expose these variables for the rest of the Jobstream Flow:
 Fig7:
Fig7:
 Fig8:
Fig8:
 Fig9:
Fig9:
 Fig10:
Fig10:
STORE_CERT_DETAILS:
This Variable Table Update Job would update a Variable Table named CERTDETAILS also associated at the Jobstream level, which would update variables like CERTAPPLYDATE, CERTPATH, CERTNAME, CERTAPPLYTIME in the Variable Table from the exposed variables from the previous set of STORE Jobs:
 Fig11:
Fig11:
CERTAPPLY Job:
This job would generate a certificate based on the certificate path and certificate name passed as arguments while also generating a certificate signing request:
 Fig12:
Fig12:
Joblog from execution:
Joblog from execution :
===============================================================
= JOB : MASTER_DA#CERT_REQ_MGMT[(1157 10/22/21),(0AAAAAAAAAAABPKT)].CERTAPPLY
= USER : root
= JCLFILE : /home/testhwa/certcreate.sh /home/testhwa oct_2021
= TWSRCMAP :
= AGENT : DAUNIX
= Job Number: 789034989
= Fri 10/22/2021 11:58:26 CEST
===============================================================
PATH=$1
+ PATH=/home/testhwa
CERTNAME=$2
+ CERTNAME=oct_2021
JKSEXT=”.jks”
+ JKSEXT=.jks
JKSFILE=`echo $CERTNAME$JKSEXT`
echo $CERTNAME$JKSEXT
++ echo oct_2021.jks
+ JKSFILE=oct_2021.jks
cd ~testhwa
+ cd /home/testhwa
/bin/keytool -genkey -alias $CERTNAME -keyalg RSA -keysize 2048 -keypass changeit -keystore $JKSFILE -validity 365 -storepass changeit -dname “CN=EU-HWS-LNX242, OU=HCLSoftware, O=HCLTechnologies, L=IN, ST=KA, C=IN”
+ /bin/keytool -genkey -alias oct_2021 -keyalg RSA -keysize 2048 -keypass changeit -keystore oct_2021.jks -validity 365 -storepass changeit -dname ‘CN=EU-HWS-LNX242, OU=HCLSoftware, O=HCLTechnologies, L=IN, ST=KA, C=IN’
keytool error: java.lang.Exception: Key pair not generated, alias <oct_2021> already exists
/bin/keytool -certreq -keyalg RSA -alias $CERTNAME -file oct_2021.csr -keystore $JKSFILE -storepass changeit
+ /bin/keytool -certreq -keyalg RSA -alias oct_2021 -file oct_2021.csr -keystore oct_2021.jks -storepass changeit
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using “keytool -importkeystore -srckeystore oct_2021.jks -destkeystore oct_2021.jks -deststoretype pkcs12”.
/bin/keytool -export -alias $CERTNAME -keypass changeit -keystore $JKSFILE -storepass changeit -file oct_2021
+ /bin/keytool -export -alias oct_2021 -keypass changeit -keystore oct_2021.jks -storepass changeit -file oct_2021
Certificate stored in file <oct_2021>
Warning:
The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using “keytool -importkeystore -srckeystore oct_2021.jks -destkeystore oct_2021.jks -deststoretype pkcs12”.
===============================================================
= Exit Status : 0
= Elapsed Time (hh:mm:ss) : 00:00:01
= Job CPU usage (ms) : 957
= Job Memory usage (kb) : 32980
= Fri 10/22/2021 11:58:27 CEST
===============================================================
SERVICENOW_POST_CHANGETICKET:
This is a RESTFUL Post job would Post a Change Ticket on Service Now with the details extracted from HWA Variables like Date and Time of the Certificate Application , Certificate Name , Certificate Path , Keystore Details etc. It would also post a generic Implementation Plan and Backout Plan in the change for a normal Certificate Application to a jks keystore.
 Fig13:
Fig13:
 Fig14:
Fig14:
Joblog from Exceution:
===============================================================
= JOB : MASTER_DA#CERT_REQ_MGMT[(1157 10/22/21),(0AAAAAAAAAAABPKT)].SERVICENOW_POST_CHANGETICKET
= TASK : <?xml version=”1.0″ encoding=”UTF-8″?>
<jsdl:jobDefinition xmlns:XMLSchema=”https://www.w3.org/2001/XMLSchema” xmlns:jsdl=”https://www.ibm.com/xmlns/prod/scheduling/1.0/jsdl” xmlns:jsdlrestful=”https://www.ibm.com/xmlns/prod/scheduling/1.0/jsdlrestful” XMLSchema:text=”resolveVariableTable” name=”RESTFUL”>
<jsdl:variables>
<jsdl:stringVariable name=”tws.jobstream.name”>CERT_REQ_MGMT</jsdl:stringVariable>
<jsdl:stringVariable name=”tws.jobstream.id”>0AAAAAAAAAAABPKT</jsdl:stringVariable>
<jsdl:stringVariable name=”tws.job.name”>SERVICENOW_POST_CHANGETICKET</jsdl:stringVariable>
<jsdl:stringVariable name=”tws.job.workstation”>MASTER_DA</jsdl:stringVariable>
<jsdl:stringVariable name=”tws.job.iawstz”>202110221157</jsdl:stringVariable>
<jsdl:stringVariable name=”tws.job.promoted”>NO</jsdl:stringVariable>
<jsdl:stringVariable name=”tws.job.resourcesForPromoted”>10</jsdl:stringVariable>
<jsdl:stringVariable name=”tws.job.num”>789034990</jsdl:stringVariable>
<jsdl:stringVariable name=”CERTNAME”>oct_2021</jsdl:stringVariable>
<jsdl:stringVariable name=”CERTAPPLYTIME”>0800</jsdl:stringVariable>
<jsdl:stringVariable name=”CERTAPPLYDATE”>10/23/2021</jsdl:stringVariable>
<jsdl:stringVariable name=”CERTPATH”>/home/testhwa</jsdl:stringVariable>
</jsdl:variables>
<jsdl:application name=”restful”>
<jsdlrestful:restful>
<jsdlrestful:RestfulParameters>
<jsdlrestful:Authentication>
<jsdlrestful:credentials>
<jsdl:userName>admin</jsdl:userName>
<jsdl:password>{aes}iyNVDXKy/4zfz36dywDf8YWVoxbqpS1dMvwKt9HqMsw=</jsdl:password>
</jsdlrestful:credentials>
<jsdlrestful:CertificateGroup>
<jsdlrestful:keyStoreFilePath/>
<jsdlrestful:password/>
<jsdlrestful:HostnameVerifyCheckbox/>
</jsdlrestful:CertificateGroup>
</jsdlrestful:Authentication>
<jsdlrestful:RESTAction>
<jsdlrestful:URI>https://dev114719.service-now.com/api/now/table/x_650167_change_0_change_mgmt</jsdlrestful:URI>
<jsdlrestful:method>POST</jsdlrestful:method>
<jsdlrestful:outputFileName/>
</jsdlrestful:RESTAction>
<jsdlrestful:Body>
<jsdlrestful:contentType>application/json</jsdlrestful:contentType>
<jsdlrestful:BodyGroup>
<jsdlrestful:TextBody>
<jsdlrestful:InputTextBody>{"assignment_group":"Middleware_Team","expected_start":"10/15/2021 08:00AM","description":"CertApply:oct_2021:Weblogic.jks:’/home/testhwa’","implementation_plan":"Implementation Plan : 1. Apply the below command to apply the Certificate to the Keystore : /bin/keytool -import -alias tws -file /root/<CertificateName>.crt -keystore <Keystore>.jks","backout_plan":"Backout Plan : 1. Apply the below command to revoke the Certificate : /bin/keytool -remove -alias tws -keystore <Keystore>.jks"}</jsdlrestful:InputTextBody>
</jsdlrestful:TextBody>
</jsdlrestful:BodyGroup>
</jsdlrestful:Body>
<jsdlrestful:Advanced>
<jsdlrestful:Accept/>
<jsdlrestful:JSONPropertiesGroup>
<jsdlrestful:JsonObjectResultQuery/>
</jsdlrestful:JSONPropertiesGroup>
<jsdlrestful:NumberOfRetries>0</jsdlrestful:NumberOfRetries>
<jsdlrestful:RetryIntervalSeconds>30</jsdlrestful:RetryIntervalSeconds>
</jsdlrestful:Advanced>
</jsdlrestful:RestfulParameters>
</jsdlrestful:restful>
</jsdl:application>
<jsdl:resources>
<jsdl:orderedCandidatedWorkstations>
<jsdl:workstation>D59D04CADB9611EA847C29F79A38B2EB</jsdl:workstation>
</jsdl:orderedCandidatedWorkstations>
</jsdl:resources>
</jsdl:jobDefinition>
= TWSRCMAP :
= AGENT : MASTER_DA
= Job Number: 789034990
= Fri 10/22/2021 11:58:33 CEST
===============================================================
{“result”:{“parent”:””,”reason”:””,”watch_list”:””,”upon_reject”:”cancel”,”sys_updated_on”:”2021-10-22 09:59:10″,”type”:”normal”,”approval_history”:””,”number”:”CHA0001009″,”test_plan”:””,”cab_delegate”:””,”requested_by_date”:””,”state”:”-5″,”sys_created_by”:”admin”,”knowledge”:”false”,”order”:””,”phase”:”requested”,”cmdb_ci”:””,”delivery_plan”:””,”contract”:””,”impact”:”3″,”active”:”true”,”work_notes_list”:””,”priority”:”4″,”sys_domain_path”:”/”,”cab_recommendation”:””,”production_system”:”false”,”review_date”:””,”business_duration”:””,”group_list”:””,”requested_by”:{“link”:”https://dev114719.service-now.com/api/now/table/sys_user/6816f79cc0a8016401c5a33be04be441″,”value”:”6816f79cc0a8016401c5a33be04be441″},”change_plan”:””,”approval_set”:””,”implementation_plan”:”Implementation Plan : 1. Apply the below command to apply the Certificate to the Keystore : /bin/keytool -import -alias tws -file /root/<CertificateName>.crt -keystore <Keystore>.jks”,”universal_request”:””,”end_date”:””,”short_description”:””,”correlation_display”:””,”delivery_task”:””,”work_start”:””,”additional_assignee_list”:””,”outside_maintenance_schedule”:”false”,”std_change_producer_version”:””,”service_offering”:””,”sys_class_name”:”x_650167_change_0_change_mgmt”,”closed_by”:””,”follow_up”:””,”reassignment_count”:”0″,”review_status”:””,”assigned_to”:””,”start_date”:””,”sla_due”:””,”comments_and_work_notes”:””,”escalation”:”0″,”upon_approval”:”proceed”,”correlation_id”:””,”made_sla”:”true”,”backout_plan”:”Backout Plan : 1. Apply the below command to revoke the Certificate : /bin/keytool -remove -alias tws -keystore <Keystore>.jks”,”conflict_status”:”Not Run”,”task_effective_number”:”CHA0001009″,”sys_updated_by”:”admin”,”opened_by”:{“link”:”https://dev114719.service-now.com/api/now/table/sys_user/6816f79cc0a8016401c5a33be04be441″,”value”:”6816f79cc0a8016401c5a33be04be441″},”user_input”:””,”sys_created_on”:”2021-10-22 09:59:10″,”on_hold_task”:””,”sys_domain”:{“link”:”https://dev114719.service-now.com/api/now/table/sys_user_group/global”,”val
ue”:”global”},”route_reason”:””,”closed_at”:””,”review_comments”:””,”business_service”:””,”time_worked”:””,”chg_model”:{“link”:”https://dev114719.service-now.com/api/now/table/chg_model/007c4001c343101035ae3f52c1d3aeb2″,”value”:”007c4001c343101035ae3f52c1d3aeb2″},”expected_start”:”2021-10-15 00:00:00″,”opened_at”:”2021-10-22 09:59:10″,”work_end”:””,”phase_state”:”open”,”cab_date”:””,”work_notes”:””,”close_code”:””,”assignment_group”:{“link”:”https://dev114719.service-now.com/api/now/table/sys_user_group/Middleware_Team”,”value”:”Middleware_Team”},”description”:”CertApply:oct_2021:Weblogic.jks:’/home/testhwa’”,”on_hold_reason”:””,”calendar_duration”:””,”close_notes”:””,”sys_id”:”9444a06e1b1330107394c805604bcb1c”,”contact_type”:””,”cab_required”:”false”,”urgency”:”3″,”scope”:”3″,”company”:””,”justification”:””,”activity_due”:””,”comments”:””,”approval”:”not requested”,”due_date”:””,”sys_mod_count”:”0″,”on_hold”:”false”,”sys_tags”:””,”conflict_last_run”:””,”unauthorized”:”false”,”location”:””,”risk”:”3″,”category”:”Other”,”risk_impact_analysis”:””}}
===============================================================
= Exit Status : 0
= Elapsed Time (hh:mm:ss) : 00:00:01
= Fri 10/22/2021 11:58:35 CEST
===============================================================
The above output shows the Change Number CHA0001009 generated on Service Now. Here’s the change generated on Service Now automatically:
 Fig15:
Fig15:
 Fig16:
Fig16:
CREATESCHEDULE Job:
This job would create a new Jobstream for the certificate generation taking into account the date when the certificate application is to be done and the time when the certificate is to be applied so that on the given date and time, the Jobstream executes and uses the certificate needed on the JKS KeyStore in question.
 Fig17:
Fig17:
Joblog of CREATESCHEDULE Job:
===============================================================
= JOB : MASTER_DA#CERT_REQ_MGMT[(1157 10/22/21),(0AAAAAAAAAAABPKT)].CREATESCHEDULE
= USER : wauser
= JCLFILE : /opt/wauser/createschedule.sh 10/23/2021 0800
= Job Number: 25528
= Fri 10/22/21 12:00:50 CEST
===============================================================
WA for UNIX/JOBMANRC 9.5
AWSBIS307I Starting /opt/wauser/TWS/jobmanrc /opt/wauser/createschedule.sh 10/15/2021 0800
IBM Workload Automation(UNIX)/JOBINFO 9.5.0.02 (20200410)
Installed for user “wauser”.
Locale LANG set to the following: “en”
/opt/wauser/createschedule.sh 10/15/2021 0800
IBM Workload Automation(UNIX)/COMPOSER 9.5.0.02 (20200410)
Licensed Materials – Property of IBM* and HCL**
5698-WSH
(C) Copyright IBM Corp. 1998, 2016 All rights reserved.
(C) Copyright HCL Technologies Ltd. 2016, 2019 All rights reserved.
* Trademark of International Business Machines
** Trademark of HCL Technologies Limited
Installed for user “wauser”.
Locale LANG set to the following: “en”
User: wauser, Host:127.0.0.1, Port:31116
User: wauser, Host:10.14.37.83, Port:31116
/
-add /tmp/Schedbuild
AWSJCL003I The command “add” completed successfully on object “js=MASTER_DA#DEPLOYCERT”.
AWSBIA090I For file “/tmp/Schedbuild”: errors 0, warnings 0.
AWSBIA288I Total objects updated: 1
AWSBIS308I End of job
===============================================================
= Exit Status : 0
= System Time (Seconds) : 0 Elapsed Time (hh:mm:ss) : 0:00:01
= User Time (Seconds) : 0
= Fri 10/22/21 12:00:51 CEST
===============================================================
Schedule Created Automatically:
Jobstream named DEPLOYCERT created automatically and scheduled for 23rdOct:
 Fig18:
Fig18:
Conclusions from the Use Case:
Certificate generation, an application can be completely automated end to end through HWA.
HWA can be an end to end Orchestrator for change creation and change implementation as well.

Fig19:
Start a Conversation with Us
We’re here to help you find the right solutions and support you in achieving your business goals.







